A Comprehensive Guide to Building Secure Systems and Applications
Most Android security failures aren’t caused by bugs. They’re caused by design decisions made too early and questioned too late.
Blog posts teach you how to patch individual vulnerabilities. Official documentation explains API features. But neither tells you how to think about Android security as a system—from the application layer down through the framework to the HAL.
That’s the gap most developers face: You know the basics, but when you’re in a design review and someone asks “what if an attacker compromises this service?” or “how do we prevent privilege escalation here?”—surface-level knowledge isn’t enough.
You need to understand Android’s security architecture at a system level. Not just what to do, but why the architecture works the way it does, where it breaks down, and how to design defensively when standard patterns don’t apply.
That’s exactly what this book provides.

What You’ll Get:
Comprehensive Coverage — Essential security principles and methodologies tailored for Android development across automotive and mobile devices. This isn’t generic security theory—every chapter addresses real systems you’ll actually build.
System-Level Security Insights — Deep understanding of security architecture from application layer to HAL. Most resources stop at the API. This book teaches you how to reason about security across the entire stack, from framework services to hardware abstraction layers.
Practical Guidance — Real-world scenarios and actionable strategies to address security challenges effectively. Four complete case studies—Financial Android Application, Key Provider Service, Sensor HAL Layer Daemon, Vehicle Data Logger Application—show exactly how to apply concepts to production systems.
Threat Assessment Tools — Modern tools and techniques for threat mo
Table of Contents:
- Brief
- The Big Picture
- Principles and Methodologies
- Securing the Development Lifecycle
- Threat Modeling, Standards and Guidelines
- Attack and Defense
- Common Programming Mistakes
- Data Validation
- Android Security Model
- Protecting Data
- Authentication, Network, and Protocols
- Practical Scenarios
- Compiler and Tools
- Last Word
- Appendix
- Abbreviation
- References
Quick Comparison
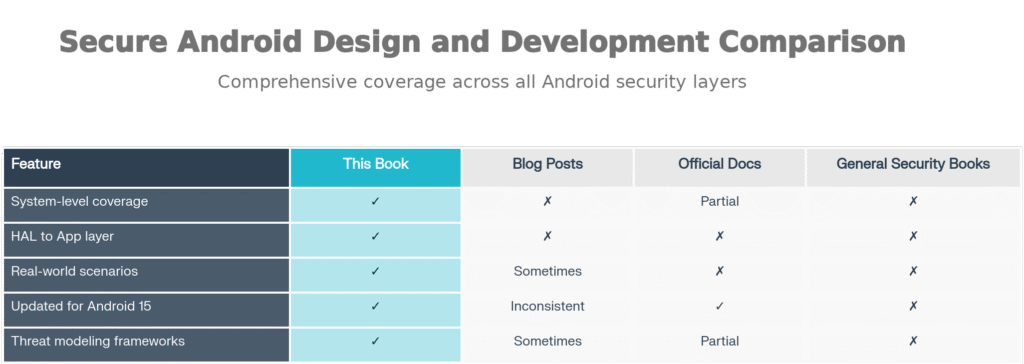
Check the link below to buy the book.
https://leanpub.com/secure-android-development
Free Sample Chapters
Why Buy with Confidence
✓ Android 15 aligned — Updated April 2025, stays current with platform evolution
✓ 60-day money-back guarantee — Zero risk, full refund if unsatisfied
✓ PDF + EPUB formats — Read on laptop, tablet, phone, or Kindle