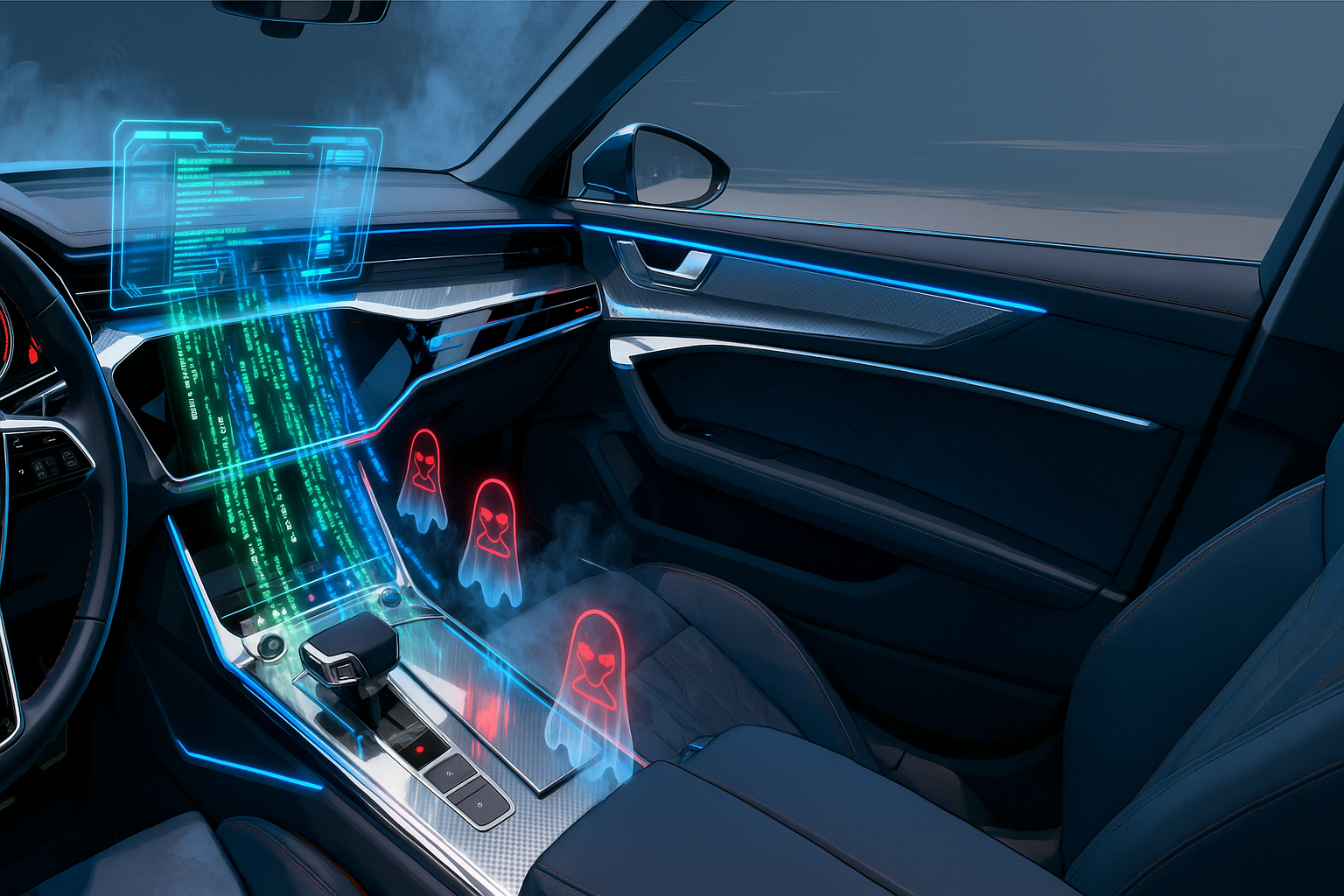
In 2016, Citizen Lab received a request forwarded by Ahmed Mansoor, an Emirati human rights defender. It was a request to analyse a suspicious message. The message contained a malicious URL. The Citizen Lab researchers, with help from Lookout, discovered that the link could trigger a chain of three unknown iOS zero-day vulnerabilities. It could lead to having complete control of the device, such as calls, emails, GPS, camera, microphone, etc.
It was confirmed later that it was Pegasus, a commercial spyware developed by NSO Group could target Android and iOS mobile phones. Later on, the other discoveries showed it wasn’t the first time that Pegasus used to target people, and of course, not the last time. Pegasus has evolved and improved over the years and adapted itself to new versions and new vulnerabilities.
Pegasus has been improved from a one-click spyware to a zero-click one in recent years. To be frank, we could call it a dark art. It requires systematic research and improvement to keep it updated. It’s not only an application, but that is a complete chain from the first exploit till installing new packages and handing over the control to an agent/user through a server-based utility. The attacker could collect lots of information from the victims. That’s horrible but it is reality as well.
Understandably, each technology has its pros and cons. Hardening the product is the developers’ and designers’ duty. We need to identify the complexity of the industry as we are developing the product, as each area needs its special considerations.
The user’s privacy and keeping the user data secure are crucial. But in Automotive, alongside security and privacy, we need to think about safety as well. We might be able to say that it comes first since that’s about human life. Imagine what could happen if Pegasus or an Automotive version of that could compromise an Infotainment system. Then, the outcome is not only getting access to GPS data, a microphone, etc. It could interfere with the vehicle’s internal network — even critical functionalities. The next step could be having some malicious application on other ECUs. It might be difficult, but that’s not impossible.
What are the lessons for Android Automotive?
More frequent updates
Most of the car manufacturers are not delivering the latest Android version. Plus, they are able to keep updating the Infotainment system with security patches once something is out by Google. What’s more is that the car owners don’t usually update their infotainment regularly.
Architectural hardening & security mindset
As we discussed, zero-day vulnerabilities are the first candidates to compromise the system. But having security considerations for the whole system in mind while we are making architectural decisions could reduce the impact of the exploits.
Disabling unnecessary facilities
For instance, downloading files by users might not be meaningful in an Infotainment system. Especially since the applications are restricted and it is not supposed to work as a mobile phone. But there might be other ways around such browsers, email apps, etc, that could load some files.
Beyond the technical architecture, collaboration maturity matters just as much. Google is playing the main role in Android design, development, and security. They are actively providing the security patches and supporting the bug hunters. While the Google partners are helping to find the vulnerabilities, any improvement in cooperation from the automotive companies could be helpful to take it further and more promising. At minimum, automakers should allocate dedicated budgets for Android security or running some programs, and the long-term plan could be having security teams analysing, monitoring, and providing solutions for the real-world problems that are evolving quicker than before.
There is a long list of what should be considered to keep the in-car Infotainment systems secure and safe. Pegasus mastered adaptation across layers — from exploit to control that Android Automotive must mirror that adaptability defensively faster than the threats that evolve around it.